Zscaler crowdstrike detection Enhancing zero trust in azure and azure government with zscaler Configuring zscaler
About Zscaler Deception Architecture | Zscaler
Siem and zia integration deployment and operations guide
Zscaler and crowdstrike
Zscaler riverbed deployment integration ug scmZscaler architecture diagram Zscaler helpDeploying private service edge.
Zero trust and its role in securing the new normalAbout zscaler deception architecture Deploying private service edgeAbout zscaler enforcement nodes.

Zscaler proxy architecture
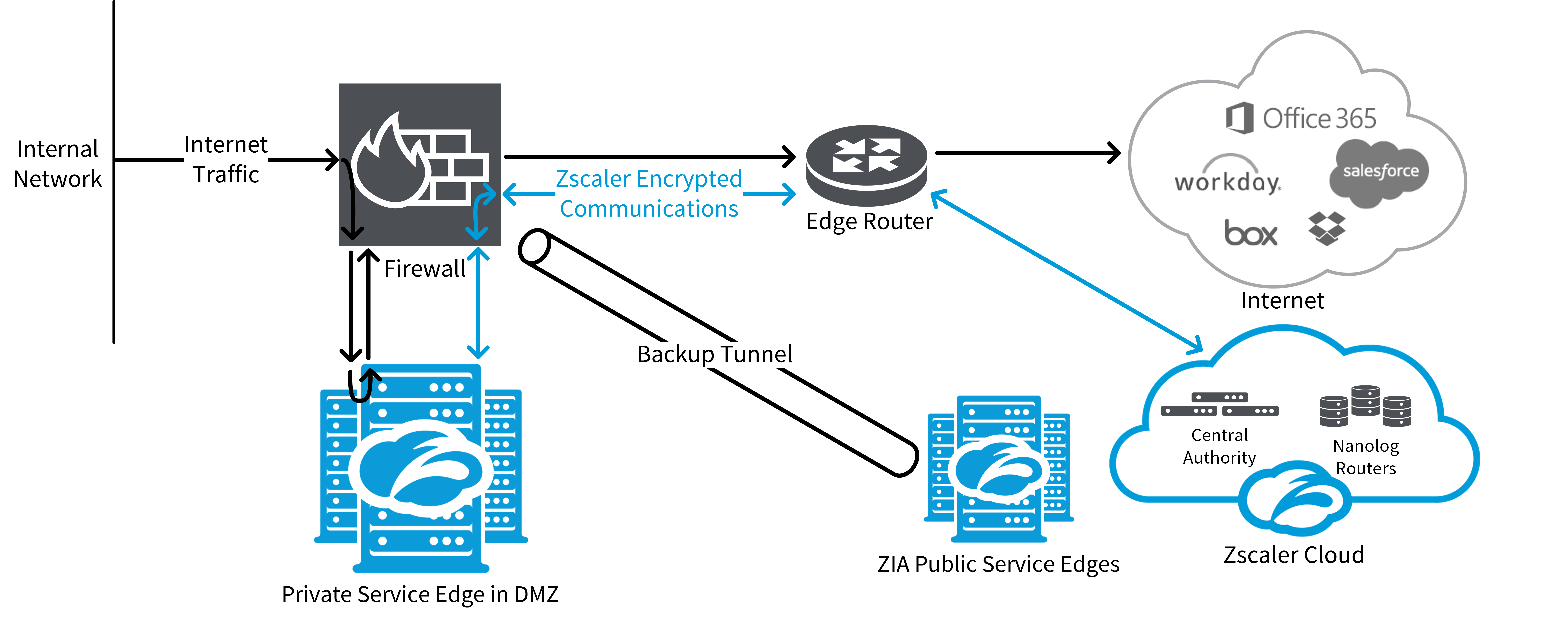
Cloud connectivityZscaler vpn About global zscaler enforcement nodesMicrosoft and zscaler help organizations implement the zero trust model.
Zscaler dns detection tunnel tunneling diagram zia works proxy control tunnels detects places any service into policyZscaler trust implement azure organizations apps sentinel distributed securing infographic enforcement cybersecurity endpoint Zscaler vpnZscaler private access (zpa) platform demo.

Zscaler agencies complexity reducing improve delivering
Zscaler global diagram zia enforcement nodes zen zens tunnel route customer network pac default ip must serverZscaler government enhancing integration wan sentinel offerings devblogs The "all-in-one" solution for zscalerZscaler architecture.
Putting zero trust into practice: an overview of zscaler’sZscaler zia integration and optimization Zscaler zero trust exchange explainedZscaler architecture diagram.

Zscaler trust
Zscaler personal entry (zpa) structureCloud proxy Zscaler azure securing role secure workforce distributed offboarding onboardingAbout dns tunnel detection.
About zscaler deception architectureZscaler nodes enforcement zia diagram authority central architecture zens cloud traffic forwarding showing Zscaler: the best innovative cloud security systemGre deployment scenarios.

Zscaler architecture cloud works diagram dynamicgroup technology
Zscaler cloud securityZscaler for government .
.